It’s easy for small to medium-sized businesses to think that since the company is smaller, cyber criminals will skip attacking the enterprise. But, SMBs are suffering from attacks of malware, ransomware, external threats, and data breaches. With absence of security measures among SMBs, the possibility of remaining unaffected by cybercrime is grim.
Keep reading this post to learn how SMBs and MSPs are servicing this issue and a few tips of how to improve security.

Why are small to medium-sized businesses being targeted more than larger ones? Most attacks are to get personal data to use elsewhere. Larger companies have more data to steal, but smaller businesses have less secure networks which makes it easier to breach a network.
Why Security Matters:
A quick look into an SMBs office shows how necessary IT solutions are to the company’s success.
Without having email/other communication systems, productivity applications and enterprise tools that do everything, it could delay success and profitability. Despite this, many companies view IT Security as an unwanted cost rather than a helpful tool for business solutions.
IT matters to SMBs and security matters to IT success.
In this technology advanced world, a SMB can use new technologies to utilize new capabilities, increase efficiency and cut down costs. Each new application creates the need to secure users, data, and environment that the solution integrates into.
Those who view security as a difficult task each time a new technology is proposed, will be slow to adopt and profit from new efficiencies.
SMBs that end up building effective IT security are able to move quicker than their competitors. While environments without strong IT solutions will have trouble innovating and could fall behind competitors.
Why SMBs Are Targeted
According to the Verizon Data Breach Investigation Report, these are 5 of the common challenges for businesses. These include:
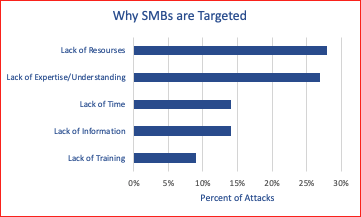
The common issue on why SMBs are an easy target is because there is a lack of something.
- Lack of Resources
Many SMBs have made the investment in systems and technology. Business owners want to avoid the extra investment into something that could require updating the whole infrastructure, storage, or operating system.
- Lack of Expertise/Understanding
Challenges that revolve around tech are becoming more complex. Companies need to use security solutions that extend to remote locations that employees may use, as well as making sure to cover roaming and mobile users. For customers that are located in different geographic regions, the problems are usually just as complex. There are partners, consultants, supply chains that go beyond a traditional network perimeter and make things harder to protect.
- Lack of Information and Training
Most SMBs don’t have a significant IT team. Security solutions with “stickiness” tend to be easy to implement and manage.
- Lack of Time
Small companies focus on operating day to day, so they can keep the business going, acquire customers, and pay employees. Medium-sized businesses often lack the knowledge from management who need to be educated on security and make resources and training a priority to ensure that their IT security needs are met.
Security Today is Only Focused on Protective Security
An effective security stance should go beyond just protecting around users, data, and networks.
Most SMBs focus on antivirus, patch management, email or web filters, application whitelisting and intrusion detection system or two factor authentications.
These are obvious protection and prevention steps you should already be taking, but it’s not enough to just do these steps.
Despite all of your best efforts, breaches can still continue to exist. Attackers improve and look for new ways to get your information and the problem is that no one could be detecting this. If there is no detecting, there’s no response.
The best strategy needs to be validated over time. Detect and react should be used to make sure that your protective measures are working.
Automated Controls
These controls take action before any damage has been done to your organization. Spending all your time trying to monitor every bit of your network and looking for anything that looks out of place is a waste of time.
It’s a costly way to operate as it requires significant IT time and resources to put suitable detection tools in place. This operation will likely raise an initial set of false positives that need to be tweaked and requires reports and meetings to make sure that detection is working.
SMBs battle against lack of time and resources. They’re better off running and monitoring solutions that offer automated controls as well as threat identification and real time response.
If something should fall outside of a set of established restrictions, the solution should automatically take action before damage is done. Not just when IT intervenes.
Approaching SMB Sensitivity
Security solutions for an SMB and MSPs servicing them, should not be any less effective that it is for an enterprise client.
There are 8-SMB friendly criteria to achieve minimum effort for maximum impact:
- Effective
- Add layers to your security strategy. Putting layers in place minimizes the chances of stopping a threat before it starts.
- Intelligence
- Choose intelligence and insights that help to spot and stop a breach.
- Automated
- If something happens outside of established restrictions, the solution you implement should take action automatically before damage is done.
- Limited administration
- “Stickiness” solutions tend to be simple to implement and intuitive to manage.
- Accurate
- There’s no time in your day to look at and solve 50 alerts a day. Your solution has to minimize false positives.
- Non-disruptive for IT
- Solutions that work with existing infrastructure don’t discourage IT teams.
- Easy adoption
- Security should be behind the scenes and protect users and their environment until the moment the user is opposing with security protocol.
- Cost effective
- Security doesn’t always come at a high cost, but it does have to be effective in relation to cost.
How Can You Improve Your Security?
- Use a Firewall
- Document Your Cybersecurity Policies
- Plan for Mobile Devices
- Educate All Employees
- Enforce Safe Password Practices
- Regularly Backup All Data
- Install Anti-Malware Software
- Use Multifactor Identification
By the end of reading this post, we hope that you have been able to learn a bit more for security for your small to medium-sized business.
If you have any questions or comments, feel free to use the section below!
Sources:
IS Decisions. (2018). The Challenge to Secure Small and Medium Sized Business (SMB). Retrieved from https://www.isdecisions.com/challenge-secure-small-and-medium-sized-business-smb/
Segal, Chelsea. (2018). 8 Cyber Security Best Practices For Your Small To Medium-Size Business (SMB). Retrieved from https://www.coxblue.com/8-cyber-security-best-practices-for-your-small-to-medium-size-business-smb/



.png?width=1080&name=GOOGLE%20REVIEW%20(1).png)